By now many of you have seen the photos and videos of the protestors turned rioters storming the US Capitol on the day of the Congressional Certification.
Ask yourself if this were your office, your company, or your client, how prepared would your company’s security or protection team have been? Does your company have the training, staffing, protocols, environmental or structural design advantages, executive temperament, financial resources, or law enforcement relationships to endure a protest, let alone a full-scale riot?
Be Prepared
The first step in being prepared is intelligence gathering. You do not always need classified or sensitive information to build a plan. Review varying news sources on both ends of the political, religious, and financial spectrum. Monitor social media, company communications, etc. Assess the protestors, do they have centralized leadership or are there varying stakeholders with different objectives flying a common flag? What are their past tactics, are the conditions similar? Do we expect your client or their organization to take a similar posture? How does law enforcement view the group or groups? Are the protestors prior security, law enforcement, or military?
Do they understand security protocols? Are they violent or merely opportunistic actors?
I do not understand some of the responses of law enforcement not being prepared before the insurrection. Washington’s events had been planned for months, and there was no secret that there would be peaceful protestors and extremist groups with a history of violence in attendance. By definition, a protest is an organized public demonstration of disapproval of some law, policy, idea, position, or state of affairs. While a riot is, on the other hand, is a public disturbance involving an act or acts of violence by generally three or more people. The act, or acts, constitute a clear and present danger of injury or damage to property.
The criminal elements of rioting, whether destruction of property, arson, looting, assault disorderly conduct, disturbing the peace, unlawful assembly, are usually covered under other laws.
Protests
During protests, stay calm and take no sides in the issue. Be firm when necessary, but respectful. Avoid confronting the protestors and demonstrating emotion. It weakens your position and acknowledges they are getting under your skin. Duelling threats only emboldens the protestors. Learn who the protest leaders are. Try to keep informed of the progress of the events. Is the group just voicing concerns or has the intensity started to elevate? Are discussions beginning to be characterized by sensationalism and tribal rhetoric? Use force only as a last resort. Have an action plan. Do not make statements or threats (remain neutral). Call the police immediately when someone breaks the law or threatens the actions of the peaceful activities of the non-protestors.
Riots
Understand the pre-incident indicators when a protest may be starting to escalate and move towards destruction and violence to become a riot. Stay calm, and do not let your actions become the flashpoint that sets off the explosive situation. Stay organized and focused, keeping yourself and the team in unison, sticking with the plan or modify it together. Make no threats, and give instructions in a clear and straightforward manner. Do not allow your actions to be misinterpreted. At no time are firearms designed to be used as a threat. And no warning shots over the bow!
What is Your Level of Influence?
One of the critical considerations in determining your protection strategy is to assess what level of relationship you have with your protectee, their management, or corporate leadership team? Can you help influence policy and protocols or are you just the security asset tasked with reactionary influence at the point of crisis? Remember our jobs are to protect the people, property, information, brands/institutions, or individual reputations. Often the higher the level of relationship with senior management, the greater your influence on the overall security and protection strategy, protocols and staffing in relation to the budget and your level of expertise.
Evidence-Based Assessments
Protests and the threat of riots often have a way of supercharging emotions. This is where evidence-based assessments are critical. They pave the way for objective-based security and protection protocols that remove emotions and foster better decision making, particularly under stress and often at the point of crisis.
One of the keys to enhancing preparation is better understanding the relationship between threats, risks, and vulnerability.
- Threat: Natural or man-made occurrence, individual, entity, or action that has or indicates the potential to harm life, information, operations, the environment and/or property.
- Risk: Potential for an unwanted outcome (loss or injury) resulting from an incident, event, or occurrence.
- Vulnerability: Physical feature or operational attribute that renders an entity open to exploitation or susceptible to a given hazard.
Threat + Vulnerability = Risk to Asset
The most important thing to calculate and assess is risk, not threat. Yes, we can talk about threat levels (and agree that say, a truck-bomb has more destructive power than a hand grenade), but what we want to know is how likely we are to encounter each of them, i.e., risk. A threat assessment should tell you if an earthquake will be more destructive than an armed attacker. A risk assessment should tell you how likely it is for your assets to be harmed by said threats.
Removing Hazards
Remove smaller items which can be used to bludgeon or serve as projectiles. Remove trash receptacles and planters which can be used to hide explosives. Remove, tanks containing flammable liquids and chemicals which can become incendiary devices. Bring company vehicles inside or relocate them to access controlled areas.
The Marshall Project looked at 50 years of protest and concluded: Disproportionate use of force can turn a peaceful protest into a violent one. Escalating force by police leads to more violence, not less. It tends to create feedback loops, where protesters escalate against police. And police escalate even further, and both sides become increasingly angry and afraid.
De-escalation, of course, does not guarantee that a protest will remain peaceful. And when protests take an unpredictable turn, it can be challenging for police to estimate the appropriate level of force.
However, the cornerstone of de-escalation strategies is transparent communication.
Former law-enforcement officials also said good policing of demonstrations is not as simple as just showing up with an approachable demeanour. “The time to make friends isn’t when you need them, you have to be in front of it.”
Staffing Considerations for Protests
- Have a sufficient “show of force” based on your intelligence gatherings and history of similar events.
- Your goal is to deter acts not to combat them.
- If senior management initially objects to the proposal for increased resource allocations whether human, equipment or financial consider preparing a damage/liability or loss profit analysis outlining the cost of destruction or injury whether in lost profits or lawsuits.
- Do not underestimate the need for relief personnel. Officers and supervisors become exhausted without good scheduling and sufficient relief.
- Establish reciprocal relationships with other vetted security firms in advance of any crisis.
- Staff turnover may well occur before the event takes place.
Law Enforcement Force Multipliers
- Explosive detection canines and handlers. The value of explosive detection canines is directly related to the ability to secure the area after the sweep.
- Mounted units have been seen as great force multipliers as they are good at moving people and gives officers an elevated perch to observe protestors.
- Bicycles units provide quick access to crowd control areas and can also be lined up as impromptu portable fences.
Crisis Management Units whether EOD, intelligence or tactical
During the breach on the Capitol in Washington, we saw a police officer taking a selfie with protestors. Another officer put on a protestor’s hat and escorted them around. We saw other officers move away barricades granting protestors access to the grounds.
Your client’s organization and the first responder community are a microcosm of life. So, expect there may be sympathizers to the cause of protestors or rioters within the client’s organization, law enforcement, national guard or other first responders. As such, keep the protection strategy, particularly the details of the safe haven or evacuation plans within the inner ring concentric rings of the protective detail.
But when we cannot mitigate the risk, we must be prepared to move swiftly in our response, as the Capitol Police and the Secret Service did with the protecting the Vice President, the Vice President-Elect, and the Congressional members.
The catalyst ultimately lies in preparation, recognition of the danger followed by effective communication. Below are the essential steps of any Emergency Response Plan. It is a progressive response model that I encountered early on through a publication called “The Bodyguard Bible.” I have since sought to add my own meaning to terms, consistent with the changing threats and the environments that we find ourselves providing protection. Particularly when we shift our focus from a solo client to securing the masses. I call this model D5, short for Deter, Detect, Deny, Delay and Defeat.
Deter – Every company, educational or religious institution needs trained vigilant capable guardians to serve as visual deterrents. To help proactively PREVENT an attack by encouraging the potential threat to choose a different location or target. This can be achieved through environmental design, i.e., circular driveways with strategically placed statues and planters which minimize a terrorist’s ability to use a vehicle as a weapon against the inhabitants of the desired structure or targeted group. However, prevention most often manifests itself through trained personnel appropriately dressed and hyper-vigilant, whether in uniform or suits. We have seen uniforms both deter in some cases and inflame in others. A general principle has often been a less militarized or tactical look closest to the public.
The situation will often dictate the tactics, but general operational footprint often consists of uniform presence, structural support (hard or soft barricades), and an emergency response team. A breach at each level will activate a different level response at a higher level.
Detect – If we can’t deter the attack, we must be trained to RECOGNIZE an attack is underway or imminent. What indicators are we noticing that a protest may be shifting toward a riot?
To detect a threat, we must move away from the traditional perimeter or lobby greeter whose only asset is a beautiful smile to trained first observers. They must be trained to recognize escalating rhetoric from the crowd, shifts in physical positioning between representative groups, the print of a firearm or the sign of a restricted gate, from a terrorist walking in a suicide vest, etc.
Deny – Once we recognize an attack is underway or imminent, we want to secure the perimeter to RESTRICT ACCESS. If the lobby hostess or concierge security officer recognizes an attack is underway, do they have the ability to send building-wide communication via a panic button, intercom or radio to help lock down the facility or alert first responders, building security, or law enforcement simultaneously?
Has the organization and security team practised lockdown procedures? This is also where clearly marked exits, and coordinated communication can help channel people away from the threat.
Delay – If we can’t deny access, then we must do everything we can to SLOW the BREACHERS DOWN by creating diversions, obstructions, barricade doors and other access points. If you cannot get your protectees out, at minimum keep them quiet and moving.
Defeat: When all else fails, you must be prepared to NEUTRALIZE the THREAT. You must have predetermined rules of engagement. Considering force, whether less than lethal or lethal, should not be an arbitrary response.
It must be calibrated against threat level and local, state, and federal laws. You may have to fight like your life depends on it, because yours, as well as the lives of those you are tasked with protecting, are at risk. If you do not have firearm consider improvised weapons (i.e., fire extinguisher, broken broom handles or other bludgeoning items, scissors, etc.) or physical aggression.
During the recent breach on the Capitol, there were three tactical considerations I noticed:
- There was an immediate securing of the Congressional chambers. LOCK IT DOWN.
- The Capitol Police and the Secret Service moved the Congressional members to their safe haven. EVACUATE THE PRINCIPAL.
- We saw at least one Capitol police officer strategically moving the mob away from the Congressional chambers. CREATE A DIVERSION.
I have heard many people comment that he should have engaged the mob with deadly force based on the crowd continuing to follow him. In this situation since he was significantly outnumbered and he still was able to execute a tactical retreat he did so, particularly since at this time, I do not think he was aware of anyone being killed at that moment. However, I do believe once the Capitol police and the Secret Service had moved the congressional members, had the rioters attempted to breach their safe haven they probably would have been met with lethal force.
What are your team’s protection protocols and use of force policies? What are they based
on, and are they consistent with local and state law? Use the incident that occurred at the nation’s Capitol as a blueprint to evaluate and tighten up your security plan.
In the Midst of Chaos
By: Mark “Six” James
Mark “Six” James is Founder and Executive Director of Panther Protection Services, LLC. He is an internationally published author, keynote speaker, security consultant to educational institutions and frequent contributor to several print, broadcast, and online media. Panther Protection Services is a full-service protection agency focusing on Risk and Crisis Mitigation, Protective Services, Self-Defense Training, and Firearm Instruction.
www.pantherprotectionservices.com
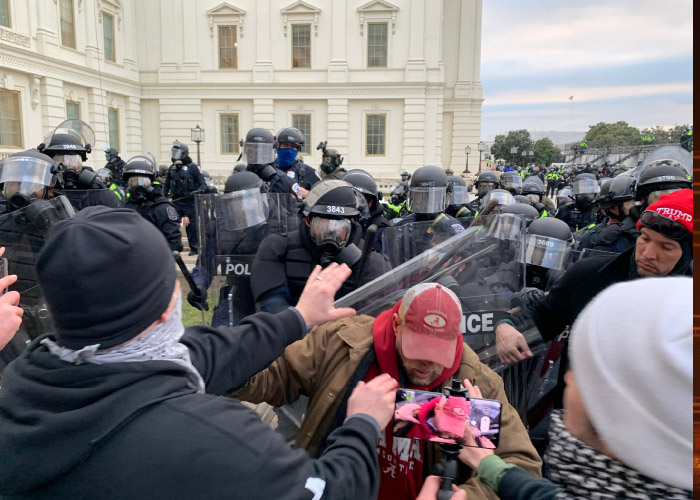

Leave a Reply