Modern Tools for a Traditional Task
Many protective service providers and law enforcement agencies have protective intelligence units that conduct investigations, manage threat assessments and provide tactical, operational and strategic analysis of the information they uncover. However, they may fail to utilize the contemporary collection and analysis methods used by today’s intelligence professionals but rather lean on the standard criminal investigation processes they have always performed. The primary causes for this would be the biases ingrained from their backgrounds and the majority of the training providers in this industry do not impart the contemporary methods and sources of protective intelligence investigations, largely due to their lacking association with today’s technological trends. While some of the dated methodologies are still valid, this article will include a review of the basic intelligence cycle, intelligence domains and discuss the purpose, sources and modern techniques that are particularly relevant to the task of protective intelligence investigations in today’s age of ‘information on demand.’
“…the most dangerous risk may be the one you did not foresee.”
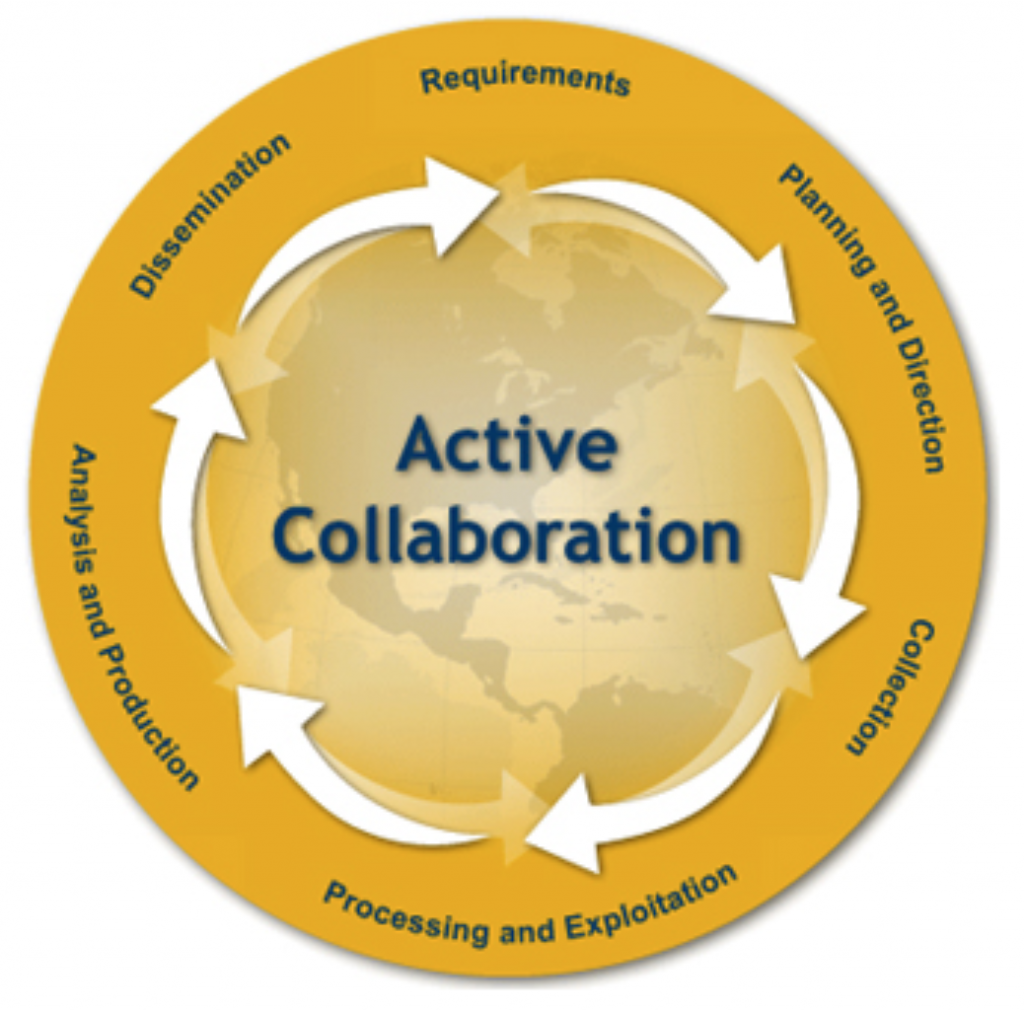
The intelligence cycle is an important process to understand for all investigators or anyone who collects information for assessment or analysis. The FBI defines the intelligence cycle as “the process of developing unrefined data into polished intelligence for the use of policymakers.” This six step cycle is a fluid progression which produces an end result greater than the sum of its parts; however, with each new step new information may develop, requiring the cycle to move backwards again before advancing. The first step is to identify the requirements in which the information is to satisfy. This step will assist with the filtering of data down to critical pieces of information by relevance. The second step is to create a plan and provide direction for the intelligence that is to come. Collection and gathering of information is the third step, which includes researching online databases, physical surveillance, conducting interviews, etc. After the information is collected comes the fourth step where the information must be processed and exploited. This means filtering the data into useable bits for the decision making processes defined by the requirements in the first step; the bits can be referred to as the “dots.” The fifth step is to analyze and convert those bits of data in order to produce raw intelligence, or “connecting the dots” if you will. The final step is to disseminate the intelligence to those who will use it for tactical, operational and/or strategic decision making.
https://www.fbi.gov/about-us/intelligence/intelligence-cycle
The Necessity of Protective Intelligence
With global security issues like workplace violence, celebrity stalking and assassinations being a growing concern, the need for protective intelligence is increasing as well. To put it simply, you cannot mitigate a risk that you have not anticipated, therefore the most dangerous risk may be the one you did not foresee. Unfortunately, bureaucracy is unforgivingly reactive and only recently have organizations begun to seek training and implement proactive measures for such incidents on a wide scale. Maintaining a preventative, proactive methodology to these issues has proven to be more beneficial and cost effective than a reactive approach. Take workplace violence for instance, in which as many as two million workers report having experienced workplace violence each year according to BLS within their Census of Fatal Occupational Injuries; of the 4547 fatal workplace injuries reported in 2010, 506 of them were workplace homicides. With U.S. companies spending more than $36 billion in direct and indirect costs of those incidents alone, the argument for how a proactive approach is advantageous to any organization is clearly legitimized.
Proactive measures taken in such cases are much more effective than response or reactive measures. For example, if given a workplace violence threat in which the terminated employee may be seeking retribution through an attack on the company’s headquarters, the typical solution would be to add extra physical security measures in and around the facility. However, a much more proactive approach would be to compliment those measures with proactive and preventative surveillance on the potential attacker. Similarly, with a stalking case, knowing the whereabouts and activities of the threatening individual could potentially restore normalcy and freedom to the life of the victim who would otherwise be locked in their own home.
“Studies of incidents have revealed that when proactive measures were not taken to protect a client, the reactive measures taken by the bodyguards failed almost every time.” – The New Executive Protection Bible, M.J. Braunig 2000
Let us define protective intelligence investigations as well as discuss the processes involved. Protective intelligence investigations differ from other kinds of investigative services primarily in how the goal is to prevent violence or a loss event, not simply reveal evidence. The individual, group or organization must collect information which will develop into the critical intelligence required in order to take preventative measures through decisive actions. This is defined by the US Secret Service as “gathering and assessing information about persons who may have the interest, motive, intention and capability of mounting attacks against public officials and figures.”
Another important aspect of protective intelligence is the source of data/information. Although most would believe ‘intelligence’ is gathered solely from secret or covert sources, the largest collection of information available to private investigators is open-source intelligence, or OSINT, which is intelligence collected from publicly available mediums. Within the intelligence community, the term “open” refers to overt, publicly available sources (as opposed to covert or clandestine sources), drawn from publicly available material, including: Internet, media, photos, geospatial information, etc. With the wealth of information available to protective intelligence investigators, a strong common sense effort should be made to focus on the information that will help answer the fundamental question of ‘does this subject present a threat to protected individual(s), group or organization?’ With the overwhelming prevalence of OSINT, there is no authority ensuring the accuracy of any information available through this domain, therefore this collection method includes a responsibility to verify, or at least corroborate, its validity.
Additional to OSINT, there are other intelligence collection domains, such as Human Intelligence (HUMINT), Signals Intelligence (SIGINT), Imagery Intelligence (IMINT) and Measurement and Signatures Intelligence (MASINT). HUMINT is the collection of data from human sources, such as interviewing witnesses or known cohorts of the suspects while SIGINT includes collection from electronic transmissions typically only done by the National Reconnaissance Office, CIA, FBI and NSA. IMINT can be a very broad domain, however for the purpose of this article we will focus on the study of imagery from sources such as Google Maps, Google images and so on. MASINT is a complex collection domain which refers to the study of weapons capabilities and industrial activities which produce measurable physiognomies, which is also primarily conducted by the NRO, CIA, FBI and NSA.
What is SOSINT?
Perhaps one of the largest and broadest fields of OSINT is the integrated technology that allows users to generate and integrate content online for collaboration and interaction for little to no cost, known as social media. The preceding explanation was to offer insight into how effective this ever increasing treasure-trove of information is to the investigator. Much broader than just Facebook and Twitter, examples of social media sites include blogs and microblogging sites, media-sharing portals, mashups, RSS feeds and podcasts. This collective source of information is growing so large within the intelligence community it is even gaining its own acronym, SOSINT for Social Open Source Intelligence. SOSINT is a content rich goldmine and a very valuable investigative tool when seeking corroborating information about individuals or groups, such as behavioral changes, interests and emulations, gang activity and general life circumstances. Additionally, a vast amount of information about criminal activities and attack methodologies for specific geographical areas is attainable through this research.
Among the popularity and proliferation of SOSINT, this domain is particularly effective to the investigator for several other reasons. The first is the immediacy in which content is not only created, but disseminated. The ‘newsfeed’ is the epitome of a media outlet for such content as there is no delay in publication and almost no restriction in its ability to spread virally. Across the myriad of social media sites, there are many methods and mediums for potential subjects to distribute thoughts or request tactical assistance, likewise there are many ways to gather information. Fortunately, the urge for most attackers to share some inclination of their plan is too great to miss; this is a process termed ‘leakage’ in which the subject may not declare his/her intentions but will share ideas, seek tactical advice, etc. Second is the facilitated interactivity and unlimited span of the audience. Never before has there been a medium in which content can be shared and banded upon by viewers as broadly and as inexpensively as it can on social media websites.
The effectiveness of social media and how it can enhance the assessment and threat management process is clearly identifiable in publications such as LexisNexis’ Social Media Use In Law Enforcement in which “survey respondents indicated several real world examples in which they prevented or thwarted pending crime, including: stopping an active shooter, mitigating threats toward school students, executing outstanding arrest warrants and actively tracking gang behavior.” For the private investigator seeking information on the behavioral circumstances of a subject, something as quick and easy as analyzing status updates, check-ins and posted photos by the subject and their friends may provide the information necessary to conclude if a legitimate threat exists.
With the billions of people registered on dozens of social media sites, it is easy to comprehend the amount of available data for anyone who knows where to look. Social media sites are so popular that you have likely conducted an investigation of some sort yourself, having sought information and assessed a tactical or even a strategic objective from that data. When your objective is a specific piece of information, sorting through all of that content can be an exceptionally hefty and time consuming burden. In order to be effective at this task, you must be able to combine resources by not only directly researching on social media sites, but using the many search engines which can do the task for you as well. With this methodology, you can easily start to connect the dots and identify the potential wheat from the chaff, enabling analytical confidence, particularly when dealing with the concern of targeted violence.
Real-Time Development Through Physical Surveillance
Mostly used as a tool for developing factual evidence to prove or disprove circumstance, physical surveillance provides information that is critical to the decision making processes for a much broader spectrum of investigations than most private detectives are used to. Surveillance is one of the oldest and most common practices within investigative services, yet it remains the best option in cases when real-time information is required. In conducting protective intelligence investigations, surveillance is a viable option in order to gather the necessary information on a subject in order to develop the appropriate intelligence.
Each of the processes of information gathering offer distinct advantages. Factual data that can be corroborated should be the focus of the collection effort and this is where surveillance out-shines other sources, such as opinions of those who are purported to know the subject. The causality is identified in the study of previous attacks, namely the attacker’s behavior prior to committing the attack. Surveillance is particularly effective in protective intelligence investigations for three main reasons. First, fewer than one-tenth of attackers have made direct threats, increasing the difficulty of validating or legitimizing the threat through other sources. Utilizing information from sources such as SOSINT will reveal the aforementioned ‘leakage,’ which are the general ideas, interests and emulations of the subject but is typically lacking in specificity. Second, research, planning and coordinating the attack is critical to the attacker’s success. The steps required in developing their plan will reveal their intentions, either in what they are doing, who they are meeting, or places they visit. Real-time information gathered in surveillance can lead to making preventative decisions sooner and more reliably than other methods of investigation. As an example, if a subject who has no historical interest in firearms obtains weapons and ammunition over the course of the investigation and then proceeds to the protected individual’s location or the headquarters building of the organization, the investigator may involve authorities immediately, hopefully mitigating the attacker’s plan before it is too late. Third, the analytical confidence from deriving conclusions based on direct observations versus assessing the quality and quantity of third party information is an important power factor. This provides the investigator and analyst a more profound confidence and less uncertainty often seen with other forensic options.
The primary objective of a protective intelligence surveillance is collecting information helpful in determining if an individual demonstrates the intent and extent (capability) to formulate and execute a violent plan of action. Once the subject is identified and background information has been collected, the main factors in which to be concentrated on during the surveillance are the current living characteristics and context of the subject’s daily routine. Areas of surveillance focus should be: factors in the subject’s life and/or environment which might increase the probability of an outburst or attack, such as living arrangements and environment; actions and behavior; daily activities and social interactions, particularly compared to possible known historical circumstances and behavior of the subject. This focus provides valuable information which will assist in the assessment of the subject’s stability. For example, if the subject does not currently have the means to satisfy the basic needs of food, clothing, shelter, social interaction, etc., then the subject may be in desperate crisis with no option left but to act out.
Examples of behaviors which may indicate coordination or planning of an attack could be: visiting others who share the same ideas and interest, visiting a site linked to the principal or protected organization, obtaining supplies or purchasing weapons. In order to be effective at surveillance, the actions of the subject must be anticipated. To that end, the investigator should make an effort to develop a list of locations and activities which may be part of the subject’s target selection or planning processes. It is important to consider the subject’s motive and mindset; where would he have to be? What would he have to obtain? Who would he have to meet with? Etc.
For violent attackers, the chances of success and escape are the predominant factors in determining the location in which to attack. Therefore, research and planning efforts intended on site selection and even tactical decisions pertaining to that site are particularly revealing during a physical surveillance. The offender will want to gain familiarity of the location, how to get there, how to escape and perhaps even take pictures of the location for reference later on in his planning process. He may even attempt to discover what the security response might be during a crisis or how effective access control is regulated, therefore performing rehearsals.
Recording and Report Writing
When compiling a report for a case as critical as a protective intelligence investigation, the investigator should include all information discovered or observed within the investigation. The information could be compiled into categories or by relevance, however it is important to include all of the information as the decision makers are the ones who will ‘connect the dots’ and make the final decision. Similarly, it is critical to record all of the subject’s activity in painstaking detail. Singular events may not be of great interest to the investigator who may have limited awareness of the larger picture; however, the totality of the subject’s actions may indicate the strategic intentions of their intended plan or perhaps tie into something not disclosed to the investigator. It is safer to take more notes and photographs than less in most cases, so bring extra memory cards and have ample note taking equipment.
As with most investigative efforts, the investigator must remain unbiased and avoid complacency. Specifically, with protective intelligence, most cases will be closed with the conclusion that an individual does not pose a significant and immediate risk to a protected person and this common ending can eventually lead to the formative bias and/or complacency. The majority of these cases are closed following the investigation, unless a criminal violation has occurred in which the case may be brought to a prosecutor or otherwise used to press charges.
To maintain effectiveness and relevance of the report, the following points should be addressed: whether or not the subject has demonstrated an interest in weapons, if he has done anything which would indicate the planning of an attack and if the subject has engaged in ominous, aggressive or stalking behaviors. In addition, the investigator’s report should address any troubling or unresolved issues such as missing or undeveloped information, or perhaps information that might clarify the subject’s lack of motives and interest in planning an attack by factual deviations from behavior that is normally associated with an attacker. Minimum data included usually includes a description of a subject’s identifiers, behaviors, interests along with current location and circumstances of their lifestyle.
Ensure that you include a document and photo log that contains the following: all documents discovered, identification photos of the target and vehicles, photos of every location the target visits along with the address of those locations and include any photos pertinent to the intent of the investigation. In most cases, your report should be written in the third person. “The investigator arrived… the investigator observed…” etc. and remember, many people will never see you but will know you and judge you by how you write and how you have conducted the surveillance.
Conclusion
For investigators, protectors and those who conduct threat assessments and evaluations, protective intelligence programs are a critical aspect of their professional life. However, when it comes to reducing violence and potential terrorist activity, we all share the responsibility of identifying, assessing and even intervening potential attackers as early as we can. The process may not be as analytical or specialized, however, in today’s world of information at your finger tips, as every person is empowered with incredibly effective tools for early recognition of potentially violent behavior and prompt preventative actions.
———————————————————
Joseph M. LaSorsa, CPP® currently employed as a senior partner managing and conducting: Protective Operations Training Courses, Executive Protection & Bodyguard Services, Risk Management Consultations & Seminars, Workplace Violence Prevention Seminars & Intervention Services, Security Consultations & Seminars, Private Investigations and Technical Surveillance Counter-Measures with LaSorsa & Associates – an International Protection, Investigations & Consulting Firm.
https://www.linkedin.com/in/josephmlasorsa


Leave a Reply