The last article Defining protection: underpinning risk & crisis management suggested some of the areas for considerations when developing plans for asset protection. Here stakeholders and the holistic approach to protection were considered posing the questions, what do we seek to protect and what are the genuine threats to these assets?
Continuing the theme we will now consider one of the simplistic security and protective models; defence in depth.
ORIGINS
Like many business and security models defence in depth originates from military terminology. Whilst this I appreciate will come as no news to many readers, in my experiences outside of the military, such terms tend to be used without acknowledging this fact. However whereas on the military front one would discuss issues such as interlocking arcs, reserves, enfilade and defilade; or Find, Fix, Strike, (Finish); the model has taken on new life in the civilian context.
Engineers for instance talk about defence in depth to plant in the shape of back-up systems, onsite and offsite resilience. Supply chains may discuss stock holdings, just in time delivery arrangements, alternative suppliers or alternative products. All indicate a similarity; a process or system that considers some of the ‘what if?’ questions and in its design attempts to add ‘defences’ to counter the unexpected based on the probabilities of elements of the system failing.
So it is no surprise then that Security, Risk and Crisis management also utilise a defence in depth model to minimise the threats to the assets they seek to protect.
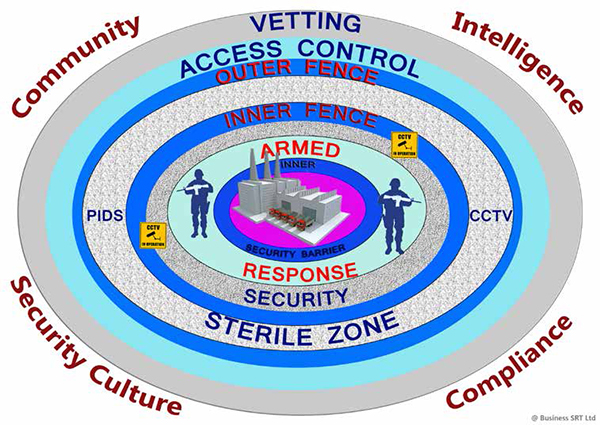
Figure 1: Defence in Depth a Simplistic model
BASIC MODEL
Staying with the theme of a high profile asset, as the holistic diagram in the last article illustrated Figure 1, shows a simplified version of this model that takes a closer look at the Security application of the defence in depth model.
When designing a protective plan we tend to start from the inside and look outward. However if we take a systematic approach we should consider this protection plan as a whole. Akin to designing training the following steps will explore this design phase from this perspective.
- ANALYSIS
- Define the end product: What is the end state we wish to achieve? e.g. Defend a vital area; protect a client; or avoid reputational damage.
- Consider the assets from the perspective of those who wish to exploit them: what are our vulnerabilities and how can these be exploited. Look at the human and cyber elements as well as the physical protective assets.
- What information is readily available to help those with hostile intent? What information can be gathered via open source and gameplay incidents based on what an adversary could plan based on such information. Don’t forget to also consider the insider threat.
- How can we protect, minimise our open source information? Historic information may already be open source, so it may be difficult to manage; however every effort should be made to minimise further sensitive information realises especially where they confirm historic data.
- What are the likely objectives of those who seek to exploit us? Intent is everything, so consider what your opposition seeks to exploit. It could be reputational and this can also be exploited via a campaign of disinformation against your client. If a full scale attack is the intent be under little illusion this will be well planned and executed. Intelligence can be limited (we don’t know what we don’t know) especially if your asset does not benefit from links to intelligence agencies.
- Identify our vulnerabilities –
- Vital assets: what are the key assets we seek to protect and how do we defend them?
- Vulnerable Areas: Where are our weaker links; how can they be exploited and how can be improve the situation?
- Vulnerable employees: do we have a system to identify employee issues or monitor changes in behaviour? Who is vulnerable to exploitation; who is disgruntled?
- Insider Threats: Do we have processes in place to protect us from insider issues i.e. two person rule rather than employing lone workers. Are cleaners or similar staff with access to all areas monitored?
- Transportation and transitional vulnerabilities: are sufficient measures in place to cover work that derogates our defences? Do we have adequate protection of assets being transported to and from our facilities?
- What assets can support us? Do we have links with external agencies? Police, Ambulance, Fire, Coast Guard, Military etc., and do we manage and maintain these relationships in order to ensure there is a true working relationship in place and clear memorandums of understandings (MOU) in place?
- DESIGN
- Community: How does what we do affect the local community? Do we manage these stakeholders well? Could be improve the situation and build better relationships where shared knowledge benefits all parties?
- Intelligence: Are we legally allowed to gather intelligence? Can we obtain information from official sources? If the answer is no then the importance of stakeholder management increases as it may be your only method of gaining local knowledge.
- Employee and visitor screening: Are measures in place to screen employees and visitors? Are these adequate? Do management pressurise Security to bring people in at the last minute without following these processes? How can these areas of protection be improved?
- Access control: Do we control access adequately? Are vital areas only open to those who need to enter them and are additional control measures in place at these points? How do we monitor and audit our control measures?
- Barriers, fences, and controlling access: Is there an adequate; efficient maintenance regime in place or is some of our equipment awaiting repair? Are the fences, barriers etc., fit for purpose and in a good state of repair?
- Deter, deny, detect, delay, defend, defeat: these common principles are key and yet the defeat element is often omitted. The best barriers, cameras and alarms will not prevent a determine adversary (whether the intent is theft, damage or attack) hence it is what you do in response to an incident that is crucial. Hence the whole system should be considered holistically. Deter, deny, detect and delay will go a long way to minimising chance encounters and incidents. When these fail assets will need to be defended and the adversaries defeated in order to bring the incident to a conclusion.
- Recovery: a rarely adequately considered or practiced element of incident management is the recovery phase. Addressing how what has occurred during an incident will affect business continuity and business recovery. Issues such as casualty handling; preserving forensic evidence; managing media issues; repairing damage (inclusive of reputational). Each aspect will take time and resources and may also leave you vulnerable to further incidents.
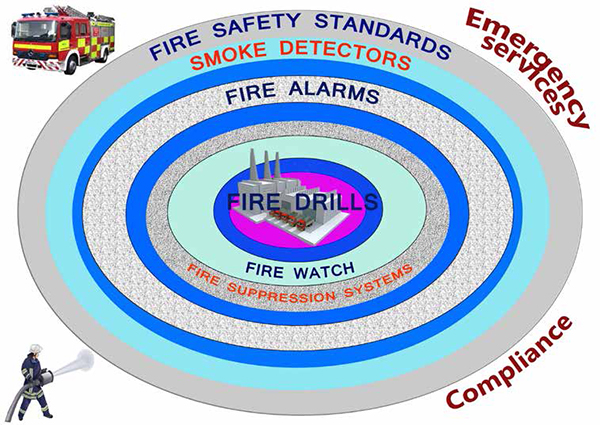
RISK AND CRISIS MODEL: Figure 2 – shows a similar layered approach to managing Risk and Crisis: in this instance a fire management system. I have chosen this one as I assume we are all familiar with fire systems, we often practice fire drills and understand fire alarms, most of us have since school. The key point here is that all emergency systems should be interwoven; creating a defence in depth model that encompasses all risks to ensure assets are protected holistically.
Figure 2: A layered approach to Fire risk (note this is not detailed but is used to illustrate how the principle can be applied to all areas of risk and crisis management).
FINAL THOUGHTS: This article provides an overview of an approach to developing a defence in depth model. It is shown using a high profile asset but the principles are applicable to any security or crisis risk management strategy. For instance when protecting your home you may consider:
- Are my locks adequate?
- Do I need a safe?
- Where do I keep spare keys?
- When I’m away can my neighbours support me? Will they?
- Do I need alarms? Should they be monitored externally?
- Do I have smoke detectors, fire suppression systems, extinguishers & blankets?
- Do I need flood boards?
- What insurance do I need if there is a theft, fire or natural disaster?
The system is basic but often we do not really analysis the real requirements against the threats or the probability of these occurring; and the consequences that would result from such incidents.
By: Paul Tonks

Leave a Reply