Smart home technology is a rapidly growing consumer and business product. Here are some figures that show projections for the growth of these devices, as well as current numbers:
- The U.S. is the largest consumer of smart home technology with a market volume of $23.5 billion in 2019 (followed by China with $12.9 billion and Japan with $4.19 billion).
- Revenue in the Smart Home market amounts to US$23.5 billion in 2019 (up 15.4% from 2018).
- The most popular products in 2019 are video entertainment (43%) followed by smart speakers (17.3%) and home monitoring and security (16.8%) while lighting and thermostat were lower on the list with 6.8% and 2.3% respectively.
- Overall the smart home market is expected to grow from $76.6 billion in 2018 to $151.4 billion by 2024, at a CAGR of 12%.
- Predictions suggest there will be 70.6 million smart home households by 2023 (nearly double from 34.8 million in 2018).
- By 2020, more than 152 million cars will connect to the internet compared to 23 million in 2014. (Alt, K. (2019, October 16))
With this growth in smart home technology, it is increasingly more important that these items are secured against cyber-attacks. Specifically, this quote from IEEE Sensors Journal explains the challenges of modern homes:
“In the past, an average home had to deal with common slash and grab criminals, while a modern home has to deal with sophisticated and tech savvy attackers who know how to find vulnerabilities and manipulate the security devices to gain access or cause distress to the inhabitants.” (Jose, A. C., & Malekian, R. (2017))
IoT devices
The devices in a smart home are known as Internet of Things (IoT) devices and the common factor among them is that they have some sort of connected communication. The IoT devices aren’t only used in private consumer environments, but in public enterprise and industrial settings as well. There are many examples of IoT devices. At the consumer level, it might include garage door openers, smart hubs, thermostats, multimedia devices, lights, appliances, and door locks. In an enterprise application, one may think of an auditorium where when you press a button, the screen comes down, the audio system starts up, a PowerPoint begins, and you are ready to present with the once click of the button. In the industrial environment, the sensors used for manufacturing all talk to each other on an assembly line and can help with precision manufacturing.
This is the epitome of true automation with all of these devices connected and communicating with each other instantaneously. You wake up in the morning and tell your smart speaker “good morning” and the lights turn, the coffee pot starts, the thermostat gets set in the bathroom for a shower, and you are given the weather forecast of the day. While IoT devices are being connected and used at an increasing rate, the safeguards to keep them secure have lagged behind. Some devices may be concerning if a hacker takes control unknowingly to you. For example, if someone knows when your smart lights turn off every morning, they know you leave the house every day at the same time. Once they know that, they can then plan to break in. The FBI in 2015 gave out a Public Service Announcement to warn about the risks of IoT devices. The Alert Number I-091015-PSA gave some examples of devices that hackers have compromised. These devices include medical devices, such as pacemakers and insulin dispensers, as well as security systems with indoor cameras. Each of these devices can cause injury if controlled or used by criminals.
Securing IoT
Securing the devices has been a challenge. Due to high demand, manufacturers introduced many IoT devices in short time frame. A 2017 article entitled Secure Smart Homes: Opportunities and Challenges, aptly summarized the challenges:
“In the last years, two more worrisome (from the point of view of security achievement) tendencies have appeared while building smart homes. The first one is the multiple connectivity to the Internet. This is caused by the cloud-based management of IoT systems as well as by the use of the cloud systems as collaborators of IoT, i.e., many IoT systems make use of the cloud for data analysis and storage.
The second tendency is the behavior of end users, who are becoming responsible for configuration of Smart Home functions including setting access passwords, granting access to devices or services (i.e., electronic door locks). This may cause security holes and instability in the Smart Home environment.” (Batalla, J. M., Vasilakos, A., & Gajewski, M. (2017))
Most IoT devices are consumer based therefore making them easy to operate and access while providing security is where most challenges come in. As with any device security, protecting devices needs to be done by both the consumer as well as the manufacturer.
There are a number of ways that manufacturers can secure their devices. These include gateway control, updates, notifications, and pushing secure access for the end user. Gateway control is commonly used by the well-known manufacturers. For example, Phillips and Lutron both use gateways for their devices to connect to and the end user to connect through. Many companies also use Z-Wave as a gateway into their devices. Z-Wave is a gateway that provides a wireless signal that only other Z-Wave devices can connect to. Manufacturers also need to undertake frequent updates to address security concerns. There are vulnerabilities coming out all the time, so companies need to protect against them regularly. Companies that provide notifications back to the end user can provide a way to secure their devices. When events are triggered, the end user gets notifications, such as attempted logins, etc. Finally, the company needs to push best practices to the end user. This can include complex passwords, password changes, allowing the notifications, and two-factor authentication, as a minimum.
The consumer also has a number of things that should be done to secure their IoT devices. The aforementioned PSA by the FBI suggests doing the following specifically:
- Isolate IoT devices on their own protected networks;
- Disable UPnP on routers;
- Consider whether IoT devices are ideal for their intended purpose;
- Purchase IoT devices from manufacturers with a track record of providing secure devices;
- When available, update IoT devices with security patches;
- Consumers should be aware of the capabilities of the devices and appliances installed in their homes and businesses. If a device comes with a default password or an open Wi-Fi connection, consumers should change the password and only allow it operate on a home network with a secured Wi-Fi router;
- Use current best practices when connecting IoT devices to wireless networks, and when connecting remotely to an IoT device;
- Patients should be informed about the capabilities of any medical devices prescribed for at-home use. If the device is capable of remote operation or transmission of data, it could be a target for a malicious actor;
Ensure all default passwords are changed to strong passwords. Do not use the default password determined by the device manufacturer. Many default passwords can be easily located on the Internet. Do not use common words and simple phrases or passwords containing easily obtainable personal information, such as important dates or names of children or pets. If the device does not allow the capability to change the access password, ensure the device providing wireless Internet service has a strong password and uses strong encryption.
Batalla, J. M., Vasilakos, A., & Gajewski, M. (2017)
(INTERNET OF THINGS POSES OPPORTUNITIES FOR CYBER CRIME)
To take this a step further, there are other recommendations from an article from Wirecutter. It suggests making sure your Wi-Fi is secure. A part of that is buying a good branded router. They will help you setup and secure your router. The above mentioned UPnP also should be turned off on a well-known router brand.
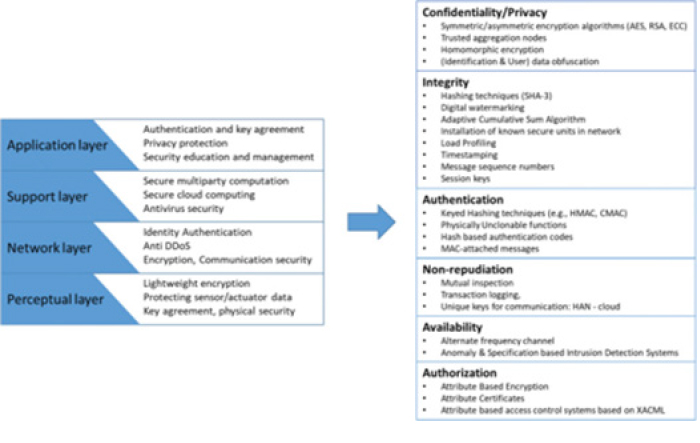
Device security uses a layered approach to making sure it is secured. The image below shows how a device might be logged into from the internet.
The devices will have a bottom to top approach with IoT physical devices sitting at the bottom and IoT services (login access) sitting at the top. Let’s say you have a light bulb it will sit on the perceptual layer. It may connect to a gateway that allows it to connect to the Network and Internet at the Network Layer. The Gateway, as well as the router it connects to, will handle opening ports, authentication into the network, and keeping it working. Next is support Layer, this is the actual communication that the devices manufacturer may setup to communicate into the device gateway of the device. Finally, there is the application layer, which may be an app on a smart phone or website. It will communicate with the support layer. The application should provide management and training to let end users understand the best practices.
Conclusion
To conclude, having a smart home isn’t something that we even thought of 10 or 15 years ago. Now, however we can connect just about any device. Many IoT devices are a luxury, and you must weight the pros and cons for each one connected. For anyone connected to the internet, it’s not a matter “if” you will be hacked, it is “when.” It may be simply having a credit card stolen, but with a smart home it may be something much more invasive. Therefore, protecting yourself with good security measures for your accounts and all devices can help mitigate an attack if it were to occur to your smart home.
Securing Smart Home Devices
By: Walter Hardy Spence, Jr
References
Alt, K. (2019, October 16). 16 Smart Home Statistics & Predictions. Retrieved from https://www.safesmartliving.com/smart-home/statistics-and-predictions/
Batalla, J. M., Vasilakos, A., & Gajewski, M. (2017). Secure Smart Homes. ACM Computing Surveys, 50(5), 1–32. doi: 10.1145/3122816
Cericola, R. (2019, April 1). How to Protect Your Smart Home from Hackers. Retrieved from https://thewirecutter.com/blog/how-to-protect-your-smart-home-from-hackers/
INTERNET OF THINGS POSES OPPORTUNITIES FOR CYBER CRIME, INTERNET OF THINGS POSES OPPORTUNITIES FOR CYBER CRIME (2015). Retrieved from https://www.ic3.gov/media/2015/150910.aspx
Jose, A. C., & Malekian, R. (2017). Improving Smart Home Security: Integrating Logical Sensing Into Smart Home. IEEE Sensors Journal, 17(13), 4269–4286. doi: 10.1109/jsen.2017.2705045

Leave a Reply