If you are a security professional with significant high-threat worldwide protective services experience, you know that depending on the client, it may not be a matter of if your client or a family member is kidnapped, but when. You also understand that it is likely that you may not even be directly providing protection for the client at the time it happens and unable to prevent it, especially when they are alone and most vulnerable.
How anonymous are your conversations, really?
Maybe you’re a close protection officer, trying to arrange a safe route through a dangerous location, or a surveillance specialist trying to communicate with others in your team.
Perhaps you just don’t trust the local government. Whatever the situation, it’ll almost certainly be easier to focus on the task at hand if you aren’t worrying about whether your messages were possibly subject to being intercepted.
Confidentiality: Personal Choice or Professional code of conduct?
Surprisingly, many people who took part in the thread commented, saying that they don’t find anything wrong with it. Some of them even named their own old clients. Others tried to justify the practice of name-dropping by saying it was a former client, or that they didn’t reveal anything personal about the client, or that they had the client’s approval to post that picture or to name the client. And finally, some said their client is already pretty well-known and paparazzi are always getting pictures of them together so why hide it? Essentially, they are good guys, and how dare we criticize people we don’t know. These were a number of the comments from individuals who either work in the security industry as operatives or own companies and hire agents to represent them.
Hiding from OSINT
It often comes as a surprise just how much is available and the nefarious uses it can be put to. OSINT can be applied towards defensive purposes, but this article will only be covering the malicious purposes (i.e. how a bad guy might get access to your client’s sensitive information and data).
One of the biggest challenges of OSINT is not merely recognising it as a threat, but encouraging the behavioural change needed to protect against it widely enough. It is not simply enough for a principal to stop posting Instagram pictures of their travels in order to hide them. Their colleagues, friends, family, and employees also need to be aware and cautious with information which could be misused.
Insecure Smart Houses
They are only of limited relevance today, but as the technologies involved become more widespread and implemented into every facet of life they will only become more prevalent. While it sounds like the stuff of science fiction, these threats exist now and are not going to go away.
For simplicity, we’ll say that a ‘smart’ device is anything which connects to the internet (or a network) and is not intended to be a computer interface. Intended is the key word there, as many of these devices are insecure for the simple reason that they are a computer. The problem is that it is now cheaper and easier to put a general purpose computer into a device and run some software to, for example, turn lights on and off than it is to design a single-purpose lightbulb which also connects to a network.
Executive Protection Realities of the Industry and the Ugly Truth
Many newcomers in the protection business have a completely different idea of what the profession is, based on what they have heard or what Hollywood tells them it is. This lack of “truth” either leaves them disappointed or leaves them vulnerable to making mistakes while on duty.
It is common in our industry to see many of our colleagues posting pictures on the internet social media sites of “selfies” taken in first-class airline seats or the client’s private jet. More selfies show them with their feet up on a suitcase claiming ‘’another flight”, or posting from 5 and 6-star hotel rooms, or fine-dining restaurants, or next to a limousine parked in front of a private jet.
How modern technology is advancing our craft
Some readers may have guessed at the participants in the above scenario or even been a part of such a detail in the past. No matter what, it’s plain to see that helicopters are an amazing tool to have at your disposal for your motorcade movements. They can advance the route in real time from a bird’s eye view, which is a great way to go from the known to the known with a good idea of the terrain you will be encountering.
However, the truth is, the simulated communications you just read were not with a helicopter, but instead were between an Executive Protection team, and it’s FAA (Federal Aviation Administration) Licensed and experienced UAV (Unmanned Aerial Vehicle) Pilot. Executive Protection is evolving every day, and one of the areas out front is technology. Developing are new forms of detection, tactical hearing and visual aids, vehicle security and transport, radio systems, and now UAV’S.
Cybersecurity Series – Artificial Intelligence, Machine Learning, and Bias
In this article, I’ll take a look at artificial intelligence, particularly the machine learning area, a basic overview of how it works, and the dangers of over-reliance on an algorithmic approach to analysis.
Event Review – Learning and Development Forum
The Circuit Magazine held a Virtual Learning and Development Forum on September 4, 2020, that was attended by Executive Protection specialists and experts from around the globe, including the UK, US, Europe, Latin America, Middle East and West Africa.
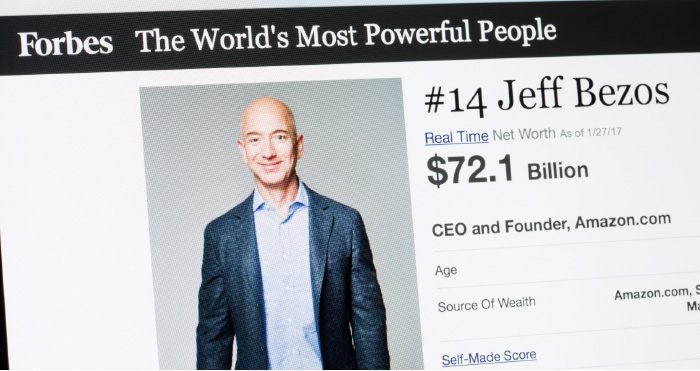
Executive Protection Fail – Jeff Bezos
The tabloid said it had evidence that Bezos has been “whisking his mistress off to exotic destinations on his $65 million private jet.
“Jeff Bezos is the founder of the online retailer Amazon and one of the richest people in the world. He has just made public that he will be getting divorced from his wife of 25 years after an extra marital affair was made public, that’s his personal business… The divorce could cost him 50% of his wealth including his stocks in Amazon, which could lead to control issues for the company and shareholders, this is company business… Again, someone’s personal life has gotten them and their company into big trouble!
Hiding from OSINT
It often comes as a surprise just how much is available, and the nefarious uses it can be put to. OSINT can be applied towards defensive purposes, but we will be looking only at malicious purposes. One of the biggest challenges of OSINT is not merely recognising it as a threat, but encouraging the behavioural change needed to protect against it widely enough. It is not enough simply for a principal to stop posting Instagram pictures of their travels in order to hide them – their colleagues, friends, family, and employees also need to be aware of the need to take care with information which could be misused.
Protecting the Principal in a Pandemic
From an operational perspective, CPs need to go back to fundamentals and apply the golden rules of protection planning and risk assessments to medical scenarios. For instance, from a strategy perspective, many HNW bought ventilators only to later discover that they would never be delivered due to shortage. So, it’s important to think how do we improve our planning and strategy from the outset to account for the unexpected? Scenarios and risks should be assessed as always in a well thought out threat matrix.
Social Media & Social Management
Social media can quickly become all things to all people meaning that one can find exactly what they’re looking for at any time, anywhere, and at the stroke of a key, or swipe of a computer screen. However, the technology can also work against you when someone is negligent in their use or management of it.
How to be Cyber Safe When on Public WiFi
Connecting your device to the World Wide Web isn’t an issue when you’re at your place. It’s relatively safe, simple to do, and free of crowded traffic. When you leave the safety of your home to a public area, the story changes. When you connect to public Wi-Fi in different places, making certain you can still connect with people, read online news, and work remotely, are you aware of the risks?
THE NEW Open Source Intelligence
We all hear about this OSINT malarkey but searching the Internet for information is much much more than just dropping a couple of search terms into Google.
There are many different search engines out there and using these various systems, combined with how you actually search for phrases, should bring you the results you are after.
The Man in the Middle – Intro to Cybersecurity
Welcome to a third article in the series looking at introductions to cyber security. We’ll be looking at a type of attack which most people will be familiar with in principle, if not in technical practice.
The basic idea is simple – an attacker sits between two trusting parties, intercepting their communication and impersonating each to the other. Obviously this is somewhat harder in practice where people are, for example, sitting in a room together, but even a phone call gives potential for an eavesdropper or impersonator.
Social Engineering and Cybersecurity
We’ll be looking at a collection of tactics used by attackers to bypass security technology by targeting the weakest link – the human in the chain.
Social engineering is really just an overly technical term for knowing how to persuade people to do something against their best interests or against their better judgment.
Keeping Your Edge – Is Politics Driving a Wedge Between Protectors?
2017 has been an interesting year for politics, particularly American politics. On these shores, we had an election for the history books, one which pitted the wife of a former President against a billionaire reality show host.
You Have a Complex Advance? Simplify It
Defining a Complex Advance All advances can be considered “complex” if you, and you should, consider all factors like the “profile” of your protecee, any credible, implied or possible threats, number of movements, personnel logistics, etc. As George Orwell said in his 1945 novel, Animal Farm, “all animals are equal, but some animals are more […]