We’ve spoken a couple of times now about tactics used to weaponise social media, and you will have spotted a pattern in these.
As with many methods used to manipulate, they do not try to argue someone around to a position in a rational manner; instead, they are designed to elicit and exploit emotional responses.
Phishing is a whole family of different attacks designed to manipulate a target into performing actions against their best interest, usually disclosing information in some way or carrying out fraudulent transactions. Within that family of different types of phishing we have:
- vishing (voice phishing over a phone call),
- smishing (phishing via SMS or text message),
- business email compromise (also known as BEC, phishing with the pretext of being a senior executive in a business),
- spear-phishing (highly targeted and personal phishing),
- whaling (highly targeted phishing against an executive),
- and many others.
The overwhelming majority of cyberattacks occur through some form of phishing. The recent, well-publicised, compromise of numerous verified high-profile Twitter accounts was enabled through a form of phishing rather than a technical exploit.
Unfortunately, as an industry cybersecurity struggles to engage with people to prevent these types of phishing schemes. Doubtless, you’ll be familiar with the some of the usual phishing training approaches, those with a quiz at the end telling you to look for typos, suspicious links, and similar protocols. These barely scratch the surface. Then, of course, there are also ‘practice’ phishing campaigns you can engage, which are usually a little more effective, but still don’t protect everyone. Generally, these campaigns, over 12 months of continuous awareness and training, can reduce response rates to a few percent of employees. The problem is that this lower response rate doesn’t last unless the training is continued, and can start to climb again as people become complacent.
What almost every attempt at training gets wrong is that they try to highlight small technical inconsistencies in phishing e-mails as the major flaws. Not only will a well-crafted phishing attempt display none of these, but they are very easy to overlook in the moment. I was recently asked to give a keynote on this issue by a company, and of the information I shared will help you understand why the technical phishing training doesn’t work as well as expected and how you can give people the behaviours and tools they need to protect themselves.
Phishing is Personal
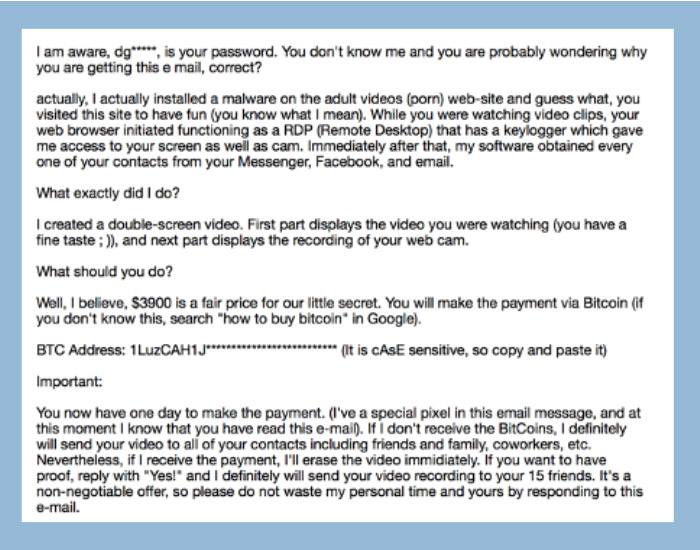
Even when phishing is a volume attack, targeted against everyone, it feels extremely personal. With the number of data breaches, it is almost guaranteed that everyone has at least one old password out there (check https://haveibeenpwned.com with your e-mail addresses to see what I mean). Bad actors take advantage of this to inject an extra personal angle into their attacks, even with modern mass attacks as the picture shows. As an example, consider being the recipient of this:
You can only imagine the effects of this type of scheme upon a person. And even where the attack is intended to take money from a company rather than an individual, it will still be intended to exploit the human recipient, not an abstract corporate entity. The people behind these attacks are only too well aware that ultimately it comes down to the person to achieve their goals.
For example, the FBI recently warned that cyber-criminals are increasingly exploiting email forwarding for BEC (business email compromise) attacks. In the case of such attacks, hackers exploit a feature in email services known as the “auto-forwarding email rules” which allow the email address owner to set up “rules” which redirect incoming emails to another address enabling hackers to gain access to sensitive emails without being detected. Syncing email settings for the web-based accounts with desktop client settings will make it harder to carry out the practice and will help protect you against this type of attack. https://www.zdnet.com/article/fbi-warns-of-email-forwarding-rules-being-abused-in-recent-hacks/
Phishing is Emotional
A phishing attack is not intended to convince the recipient through logical, sensible argument to do what the attacker wants. It is usually not intended to fool someone with perfect construction of the message. Instead, a phishing attack is meant to bypass all of that careful training, the list of rational checks to make for any e-mail, and get straight to the heart of the matter (metaphorically speaking). A phishing attack is almost always an attempt to exploit emotions, whether that’s to trigger greed over an offer, a sense of fearful urgency because an authority wants something done, hollow dread at threats of public embarrassment, or panic due to some bureaucratic hiccup.
There are two basic behaviours which can protect against the vast majority of attacks, without digging through the text looking for typos.
The first is to both trust and question your gut. If an e-mail, or any other communication, triggers an emotional response, then the automatic behaviour should be to take a step away from the communication and breathe. Once calm, start questioning the message, and the best way to do so is to contact the sender through some different, trusted means. If it’s supposedly a message from a bank, phone the bank with the number on your card rather than the one in the e-mail. If it’s an e-mail from a senior executive, get in touch with them directly, or their assistant, with details that are not in the e-mail. Better, of course, is to contact your security team with details, but there are instances where a company won’t have a team to contact.
The second is to question anything the first time. If anyone is asking for something new, a change from the usual way, then as with the emotional response above, use some other trusted channel to contact them.
These two behaviours will not protect against certain attack vectors (invoice fraud can be devastatingly effective when well-crafted), but they are two of the most effective behaviours to train to protect yourself and anyone else.
Phishing Phenomena on the Rise
By: James Bore
James Bore is an independent cybersecurity consultant, speaker, and author with over a decade of experience in the domain. He has worked to secure national mobile networks, financial institutions, start-ups, and one of the largest attractions’ companies in the world, among others. If you would like to get in touch for help with any of the above, please reach out at james@bores.com

Leave a Reply