There are various options out there for secure messaging and phone calls, ranging from expensive devices with built in hardware encryption, through to open source solutions that anyone can use. I’m going to look at, and explain how to use, one of those open source solutions – Signal.
A bit of background first. Signal was developed by the Signal Foundation as a successor to Whisper Systems’ RedPhone service, which was made unavailable in 2011 after Whisper Systems’ was acquired by Twitter. A few months later Twitter released TextSecure, and later the RedPhone software, as open source projects. Later one of the original founders of Whisper Systems left Twitter, founding Open Whisper Systems which would eventually result in the Signal Foundation and Signal.
One important note is that in 2016 Open Whisper Systems (as then was) published documents revealing that they had been subpoenaed to provide information on two phone numbers. This is only relevant as the design of the system meant they could provide the time the account had been created, and last time it had connected to the service. No message or comms data could be accessed.
It’s also worth noting that the technology behind Signal is the same as that used by WhatsApp – the key difference is that Signal is not owned by Facebook and is entirely open source, so anyone can review the code.
How it works
Signal uses phone numbers to identify contacts, however encrypted messages and calls use a data connection with a secure tunnel between participants. Intervening servers or infrastructure do not have access to the encryption keys, and so cannot realistically eavesdrop on any communications even if compromised. On Android Signal can be set up to replace your default text message client, and will handle unencrypted SMS messages as well.
Installing Signal
Signal is available through the App Store and Google Play Store, and can be installed in the same way as any other app on iOS or Android. It is also available for Windows, MacOS, and Linux desktop platforms, where the application will link to your phone for shared messaging.
iOS: https://apps.apple.com/app/signal-private-messenger/id874139669
Android: https://play.google.com/store/apps/details?id=org.thoughtcrime.securesms
Desktop: https://signal.org/download/
Step 1: Android Only Permission Setup
After hitting the install button in the Play Store and opening the app, you’ll get a permissions request for your contact list and media files. Signal does need these permissions to operate, and if you hit Continue it will walk you through the steps to grant them. You can ignore this step if you are using iOS.
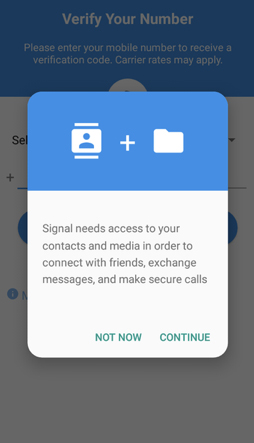
1 – Granting permissions for Android
Step 2: Verify Number
The next step is to verify your phone number. For both Apple and Android you will need to enter the number, though on Android you will be given the option to allow Signal to view SMS messages which will save you entering the code manually.
Either way once you have entered your number and clicked the button you will receive an SMS code to enter. Type it in to Signal (or automatically if you’re on Android and have granted the permission to read SMS) and it will activate. If you’re having trouble with SMS, you’ll also be given the option of receiving a phone call instead.
On iPhone after this step you will be asked to allow Notifications. Signal needs to be able to send notifications to inform you of calls or messages.
Step 3: Set up a Profile
Signal is not installed and activated. You can skip setting up a profile, or give yourself a profile name and/or avatar. These will be visible when you start new conversations, to anyone you have set up with a contact, and when you choose to share it with other users or groups. Unlike WhatsApp your profile is not public and broadly accessible to use as an OSINT source.
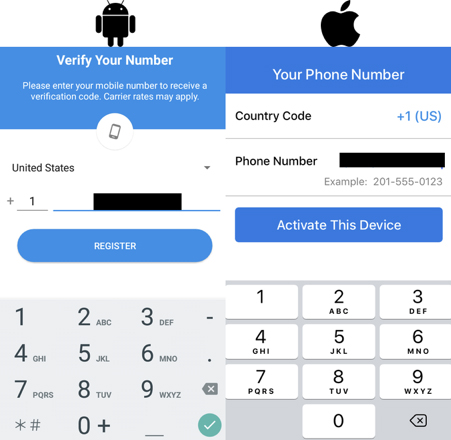 2 – Verifying your phone number
2 – Verifying your phone number
Step 4: Android Only Set as Default SMS Manager
On Android you have the option to set Signal as your default SMS app. This will not encrypt normal SMS messages, and will indicate which are secure conversations and which are insecure with the use of a padlock icon. Any contacts who also have Signal will default to secure. This is an entirely optional step.
If you do this it is very important to be aware that any contacts who are not using Signal will be sent a standard, non-encrypted text message. The same applies to phone calls placed through the app. There is an option in the settings to invite anyone you contact to Signal if they are not already using it.
3 – Set as Default SMS App on Android
Usage
Messaging
Since Google and Apple supply the underlying infrastructure, do note that while they will not be able to read contents of messages, they do potentially have access to the metadata of communications sent between parties.
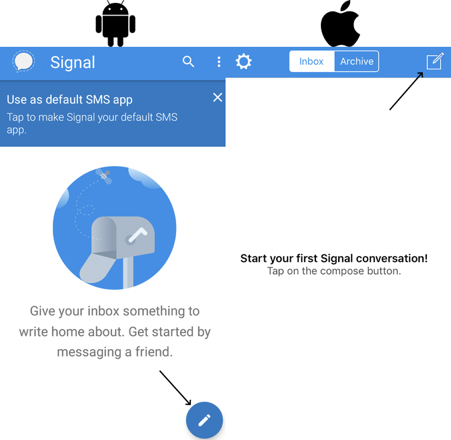
Composing a text message is similar to any other SMS you’ll send. To start off, click the relevant compose icon (bottom right on Android, top right on iPhone). On iPhone after doing this the first time Signal will request permission to access your contacts. You’ll then get a list of contacts. Tap the name of the one you want to communicate with, and you’ll be able to send end-to-end encrypted text, picture, or video messages.
Group Chat
To set up a group chat first start out as you would for a normal message, and then on Android select the More icon ( ![]() ), or on iPhone the Group icon (
), or on iPhone the Group icon ( ![]() ). You’ll then be able to add contacts to the group, or add people by phone number, and name the group. These groups function largely the same way as WhatsApp groups.
). You’ll then be able to add contacts to the group, or add people by phone number, and name the group. These groups function largely the same way as WhatsApp groups.
Making a Call
When you have a contact selected you can simply tap on the phone icon in the top right of any conversation to start a call to them. At this point, if it hasn’t been granted before, Signal may ask for permission to access the microphone. Note that on Android if you have set Signal as your default call manager app and are calling a contact who does not use Signal, the call will not be encrypted.
While the call is establishing, or once established, simply touch the camera icon to switch to a video call. The recipient may need to do the same.
Advanced Use – Disappearing Messages and Verification
There are some additional security features allowing you to send self-destructing messages (although it is important to note that nothing prevents the recipient from screenshotting the message) and to verify that no one has tampered with encryption keys. Verification requires either physical proximity to your contact, or some other way to ensure that the code they display to confirm their key is definitely theirs.
For disappearing messages simply go into the Settings menu ( ![]() on Android, or tap on the contact’s name on Apple) and you’ll be given the option to set a lifetime for messages in the conversation. Again note that this does not prevent the receiver from logging the messages, simply removes them from your phone. As Signal does not log messages on the servers, if both you and the recipient have set disappearing messages then the only traces even a diligent investigator could find of the conversation would be metadata recorded by Google or Apple showing that some kind of communication was sent between two devices.
on Android, or tap on the contact’s name on Apple) and you’ll be given the option to set a lifetime for messages in the conversation. Again note that this does not prevent the receiver from logging the messages, simply removes them from your phone. As Signal does not log messages on the servers, if both you and the recipient have set disappearing messages then the only traces even a diligent investigator could find of the conversation would be metadata recorded by Google or Apple showing that some kind of communication was sent between two devices.
How To: Secure Calls and SMS with Signal
By: James Bore
James Bore is an independent cyber security consultant, speaker, and author with over a decade of experience in the domain. He has worked to secure national mobile networks, financial institutions, startups, and one of the largest attractions companies in the world among others. If you would like to get in touch for help with any of the above, please reach out at james@bores.com.


Leave a Reply