RISK AND CRISIS MANAGEMENT SERIES
Often managers, decision-makers and even planners tend to think with a focused view within their own areas of expertise and influence. A financial manager, for instance, will consider the business bottom line and ways in which budgets can be controlled and costs minimized. Similarly, a Security manager will look at the best ways in which to protect the business assets through the use of a combination of systems and human resources. What these focused approaches create are silo mentalities.
Holistic Approach
Holistic approaches consider issues as a whole. How issues are interconnected and what impact actions in one area have on another. A key element in this is stakeholder management, looking at who is affected by plans and operations and the impact each of these stakeholders can have on the overall plan.
Stakeholders
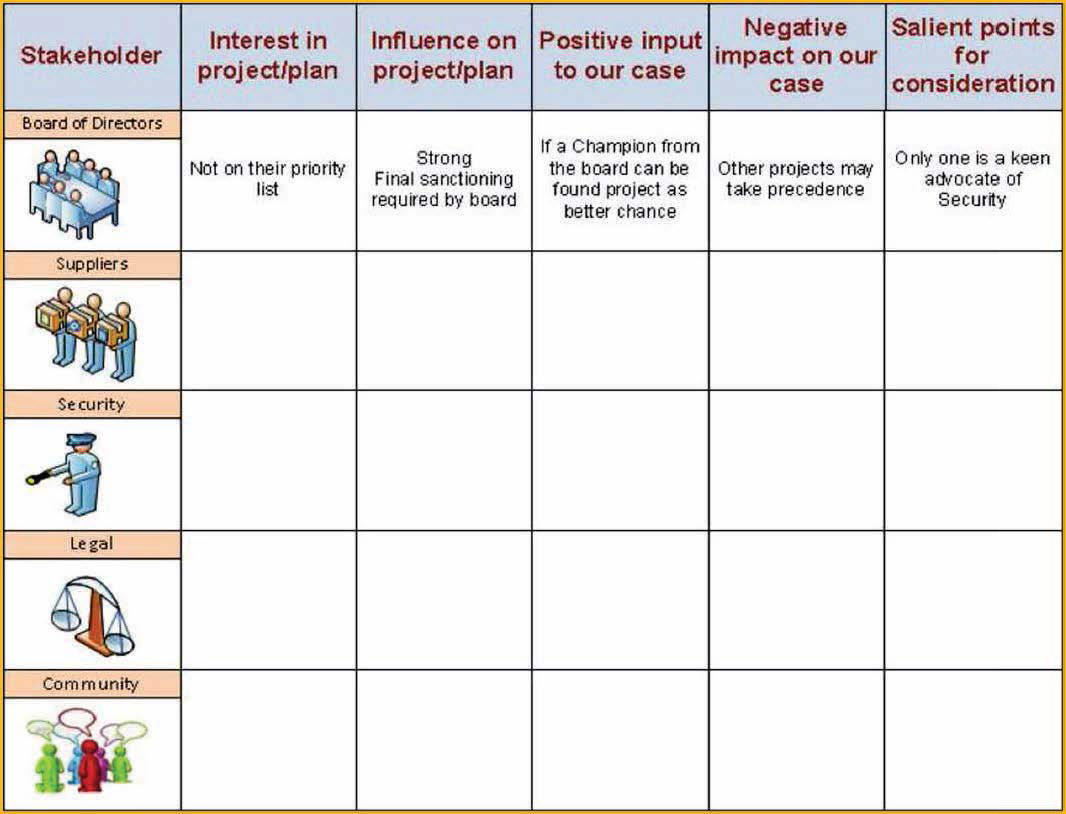
There are many stakeholder models in circulation such as Mitchell et al (1997) Stakeholder Salience or Gardner et al. (1886) Power/Dynamism Matrix. However, figure 1 shows perhaps the most basic approach. Create a table listing all stakeholders both internal and external that may be affected by your plans and consider how they may influence the overall plan or how your plan may affect them?
Figure 1: Stakeholder analysis
This stakeholder list should be extensive and consider the short, medium and long term effects of what you plan. But where does this fit with Risk and Crisis Management?
Risk and Crisis Management
Dependent upon what assets we are attempting to manage there will be a need to manage the risks associated with these assets, and measures will be required to manage these assets through a crisis.
Example
Figure 2 considers the protection of a facility that contains high-risk assets. Often planners will design the Security elements to protect these assets and though they may engage with some stakeholders: such as internal suppliers for power sources to connect Security systems; or external stakeholders such as the Company contracted to install a wall or fence. However they may not consider the water supplies to the installation, or the environmental visual impact these constructions have to house prices in the local area.
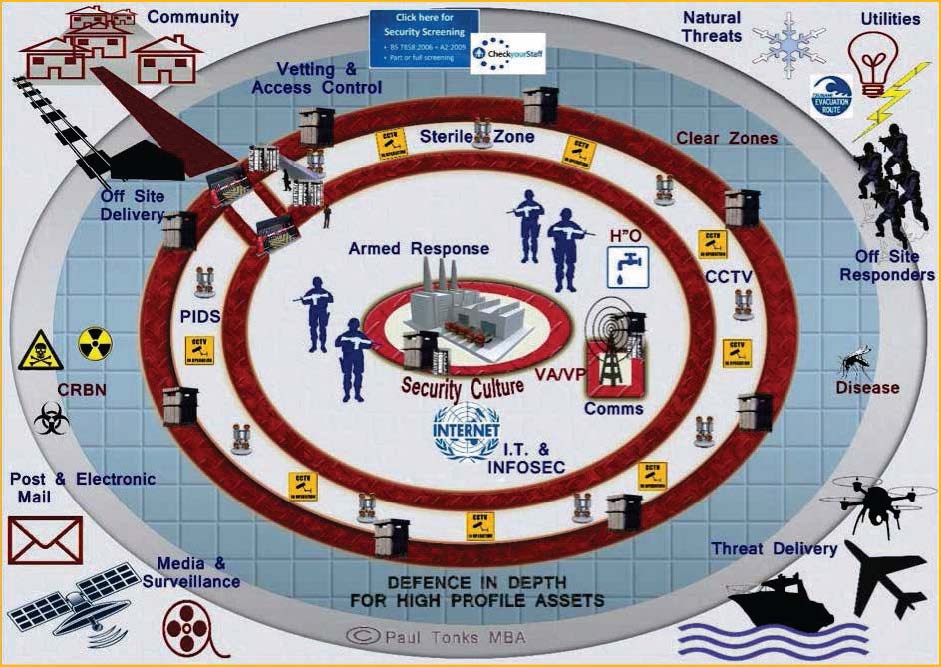
Figure 2: Defence in Depth for High Profile Assets
Failing to consider plans, projects and routine operability with a holistic eye can result in unanticipated repercussions. For example, a recent project attempting to install a protective wall in the South of England saw the project manager decide to drive the work and try and catch-up by working his team on a Sunday. The failure to consider stakeholder reactions lead to complaints from nearby residents about the noise. This resulted not only in the work being halted, and the contractors involved still having to be paid but also press interest from both local radio and newspaper journalists.
These issues really underpin the concerns that this series of articles aims to address over the coming months using a holistic approach to risk and crisis management. Figure 2 illustrates the basic model that the series will address and this layered approach to risk, security, crises and emergency management.
What are we trying to protect?
One of the first questions we must ask is:
- What are we actually trying to protect? This must closely be followed by:
- What are the genuine risks this asset has?
For instance, a wealthy business client may have excellent close protection complete with burly guards, but may in actuality be under no more risk of attack than the average person on the streets. A higher risk to that individual may come from hackers compromising information that attracts media attention, yet this information is protected by little more than a reputable software Security system.
A well-defended military camp may have interlocking arcs of fire, dominate the ground and great fields of fire. However no consideration is given to ensuring the water supply is monitored prior to consumption leaving them exposed to poisoning, or little is done to counter malaria (how many suffered from this during Op Palliser in 2000 – especially when there were no casualties from enemy action).
These brief examples perhaps highlight the biggest issue with our threat assessments. We tend to focus on an enemy or particular threat rather than consider the issues holistically asking the question what are the real hazards and risks associated with this plan, project, task or operation?
Risk
When looking at risk we should, therefore, consider not only direct risk but associated risks.
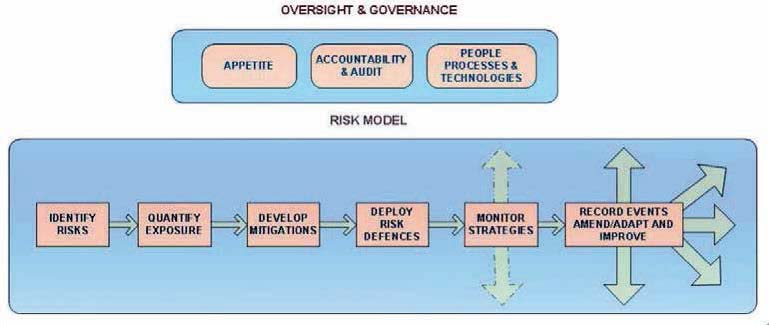
Figure 3: Risk Management – a simple model
The model in figure 3 shows a basic risk model. It covers the oversight and governance considerations which include:
- Appetite: What risks are we willing to take? Are these graded dependent upon circumstances?
- Accountability and audits: how we will ensure responsibilities are divided, implemented, evidenced and checked.
How risk is managed:
- Processes: what procedures and evidence of these procedures have been put in place? Have they been communicated? Do people understand them? Have they been trained? Are they being followed? Are they being regularly checked and monitored?
- People: Are people managing the risk correctly? Are they following our guidelines? Are personal behaviours supporting our risk mitigations? Are we doing enough to protect our people? Are we doing enough to protect third parties from the risks associated with our actions?
- Technologies: What technologies are available to help us manage risk? e.g. risk analytics. Would technology be better employed than people or would a combination of the two enhance our mitigations?
The risk model: this basic model covers the following steps:
- Identify risks: likely risk areas include:
- Operational Risk
- Value Chain risk
- Functional Risks
- Virtual Risks
- Micro and Macro environmental risks
- Low probability / high consequence risk
- Quantify exposure: in other words analyse the probability of a risk occurring, then map this against the consequences of such an occurrence. Prioritise based on highest probability (although high consequence assets e.g. CRBN related materials may result in low probability events being given the highest priority and protection).
- Develop mitigations: Assess options available, design mitigations and select those best suited to your needs. Implement a development program to adopt these mitigations inclusive of physical works, process scripting, training and evaluation, and progress monitoring.
- Deploy Risk Defences: A combined layered approach as hinted in figure 2 should be employed to protect your assets. (These will be covered in greater detail later in the series).
- Monitor strategies: Maintain an overview of short, medium and long term strategies. It is insufficient to develop, deploy and leave. The World is complex, things change quickly and so does risk. Ideally, a risk manager should be appointed to focus on the business risks.
- Record events, amend/adapt and improve: Linked to the last element is the monitoring of external events and internal occurrences. This can be to trend issues that if not addressed may grow into a future concern (ignoring issues that result in latent errors). This also includes using operational experiences from other areas to learn, adapt and continually improve your own practices.
Final Thoughts
This initial article in a series of risk and crisis management articles covers some underpinning elements that should be considered when addressing these areas. Future articles will endeavour to touch on the following areas:
- Defence in Depth
- Risk and Crises tools and methodologies
- Training and Exercise development
- Incident and event management
- Post-incident Management
By: Paul Tonks
Note: Feedback, questions and queries are welcome and the author will do the utmost to address these.

The foundation of your home is one of the most important things you need to take care of. If it were to break or didn’t take care of it properly, you could lose a lot of value. I would agree that you need to be able to access risks because you would not want to do something if it is going to hurt you.