Social Engineering and Cybersecurity
Welcome to the second article in this series looking at cybersecurity and its interaction with the protective and wider security world.
This time we’ll be looking at a collection of tactics used by attackers to bypass security technology by targeting the weakest link – the human in the chain.
Social engineering is really just an overly technical term for knowing how to persuade people to do something against their best interests or against their better judgment. An example is talking someone into handing over the password to their e-mail account, whether that’s in person, via e-mail, through text messaging, or simply watching over their shoulder as they type it out. Another might be persuading a mobile provider’s service centre to shut down someone’s account, through impersonation.
Broadly there are only a few methods in social engineering, and different ways to apply them. The most commonly seen these days due to its anonymity, effectiveness, and the ability to automate the process, is various forms of phishing. Just for some brief history, as I get asked this, the misspelling of phishing to mean this type of attack comes from the 1990s and followed the use of phreak to refer to people who exploited phone systems.
Phishing, Vishing, SMishing, Spear Phishing, Whaling
The only differences, really, between the different forms of phishing are the targeting and the method. Phishing, spear phishing, and whaling all rely generally on e-mails, whether they’re spoofing, stealing genuine e-mail addresses, or simply casting a wide net and using a disposable. Spear phishing and whaling take a little more effort and often involve researching the target.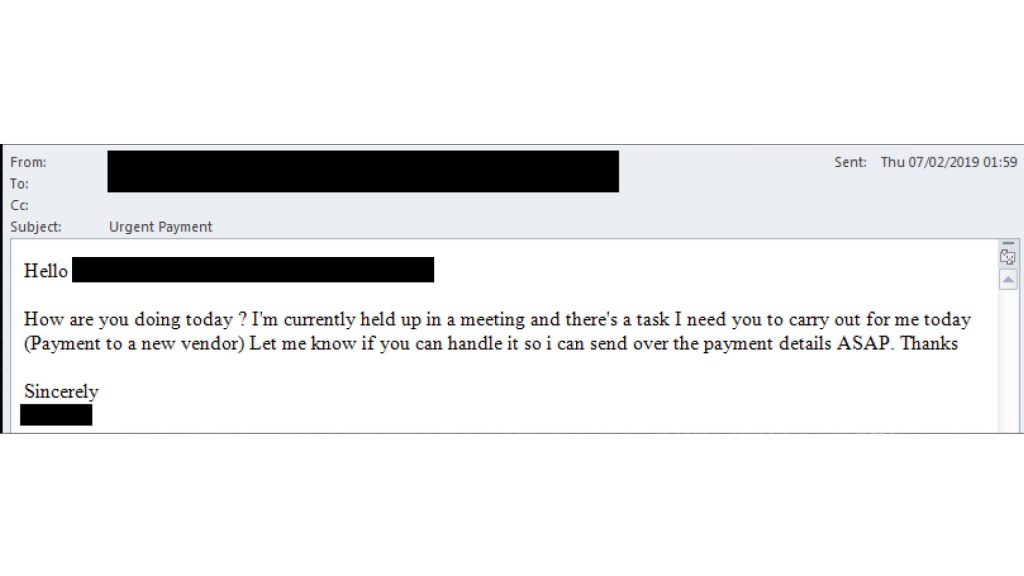
You can see a genuine example of a spear phish below, with some details hidden to protect the target. The attacker used an e-mail domain with one character difference from the genuine one – an i replaced with a j. They also researched the target company, impersonating the CFO to an employee in finance.
Generic phishing and SMishing tend to cast a wider net, relying on large numbers to catch a victim to exploit, while Vishing uses a phone call. All of them rely on a tactic referred to as pretexting, or impersonation, to persuade people to do what the attacker wants.
Watering hole attacks are another variant of phishing where instead of asking a victim to disclose information, or to download malware, an attacker will ask them to visit a website. This may end with a compromised machine, a compromised password, or a compromised user, but never well.
Whaling is similar to other phishing tactics but deserves separate mention for the sophistication of the attacks. Those who whale, targeting high profile executives, are organised and will do significant research and preparation, using open source intelligence such as LinkedIn profiles and company filings to construct organisational charts of a company’s internals. Reconnaissance will be performed by vishing at low levels to understand how the company words, and possibly to gain access, before an attack is executed. One particularly well-executed attack involved company registrations to match existing suppliers, and is known to have cost several top technology firms at least £77 million.
For a good example of some of the most common tactics Google have provided a quick quiz at https://phishingquiz.withgoogle.com
Phishing is not just used for quick financial gain, but has been used for particularly vicious blackmail campaigns – usually in a form called catfishing. In catfishing an attacker will create a profile on a dating site, designed to be appealing to a particular group of people. Sometimes it will be entirely false, others true enough to allow them to arrange video calls. Once a relationship has developed the catfish may go either for a scam, saying they need money for a plane ticket for example, or may descend into particularly vicious blackmail using previous intimate messages, images, and video exchanged. Often these scams are not detected, as victims are too ashamed to report them.
I have no idea why catfishing isn’t referred to as catphishing.
Pretexting, Tailgating, Baiting, and Quid Pro Quo
While phishing does make use of pretexting, it is generally given its own category in any attack frameworks. Phishing is electronic, and in a way simpler. Pretexting might be done via the phone, where it crosses over with vishing, or in person. There are long texts written on how to pretext, getting uniforms from different commercial companies, how to walk right to avoid too much attention, hi-vis jackets, clipboards, the right sort of conversation to make to be forgettable, and a lot of work and theory on influence and persuasion.
Tailgating sometimes falls under pretexting, with an attacker simply following people through what should be a secure door – often by carrying a ‘heavy’ box, rushing for the door, or spending ten minutes in the smoking area with a group and a fake badge.
Baiting is usually used to gain greater access or information once an attacker has performed some basic compromise. The classic example here is dressing as ‘the IT guy’ for a large office, yanking the network cable for someone’s machine, waiting for them to ask for help, and then simply suggesting they get a coffee as this will take a while. It is a method of setting up an opportunity to further compromise a target, and closely related to quid pro quo.
Quid pro quo can follow a baiting attack, or be entirely separate. It is a method that works on the basic human need to reciprocate help that we receive – whether that’s fixing a computer, or being given a gift.
Some penetration testing companies will offer physical pen testing, and red teaming, where they will try to exploit all of these tactics (and more) to gain access to a designated target, before reporting exactly how they have done so and where to improve in future.
I have very rarely heard of them failing to get access to a target area, and they are always pleased to have an attack effectively shut down before it completes.
Whole books have been written on social engineering tactics, some of them well worth reading, so here I’m only trying to give a basic overview. Hopefully you’re now better informed on some of the methods, and how these relate to both cybersecurity and wider security. Next time I’ll be digging into man-in-the-middle attacks, a less common but devastatingly effective method of compromising information and people.
Intro to Cybersecurity Part 2 – Social Engineering and Cybersecurity
By: James Bore
James Bore is a cybersecurity ‘Jack of all trades’ by vocation and choice. In over a decade he has gathered experience meandering across a range of industry sectors, organizations, and disciplines in IT, always with a focus on championing and improving security. Currently, he works for an entertainment and hospitality company, and in rare spare time runs a blog on cybersecurity https://coffeefueled.org

Leave a Reply